|
: Spam Warrior :
: Here's what turned up in my queries. I've highlighted
the important
: bits again.
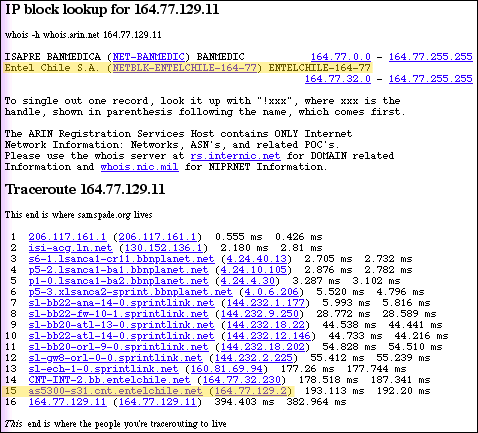
samSpade_results.gif
: You'll want to look through the Whois and the IP Block
information to see
: what ISP the spammer is using (assuming the IP address wasn't spoofed).
: Here, the top highlight tells me that I'm looking at a spammer in
Chile because
: that's where the service provider is located that initially forwarded
the email.
: The bottom highlight shows us the exact IP address of that forwarding
machine.
: The double reference for the IP Block look-up means that two parties
are listed
: as 'owning' that range of IP addresses. We're going after the second
one
: because the machine just upstream from our target is from that domain
name.
: Another point worth mentioning is that if the Traceroute returns a
"* *" for any
: hops across the network, that means that the machine at that hop is
not
: responding to Traceroute. That's either because it's mis-configured
(unlikely),
: set to ignore Traceroutes (possibly), or isn't connected to the network
(i.e. a
: modem connection). The latter can be frustrating, but do a look-up
on the
: last solid IP address logged - a lot of times, that will be their
ISP.
: Since we didn't get any contact information with this
sweep, we'll have to dig
: a little deeper; what I'm looking for is an email address to send
a message
: to regarding system abuse.
: Another point worth making is that in some states (Washington,
particularly)
: it's possible to get money out of this sort of venture. That's right!
You can
: get up a $1,000 a pop, and many spammers will settle out of court
for a
: little less than that. There was a fine article written for the NYTimes
that
: covers that, and also helped me get started with this business (see
the
: references on page 3).
: Mr. Spammer, in Chile, with the spam/virus :
: Let's find out a little more about Entel Chile S.A.
SamSpade will automatically
: enter the appropriate information into a new search page if you click
one of
: the links from the search results page. This time, we want the specific
contact
: info, so we'll use the GeekTools' Whois server as such :
samSpade_whois.gif
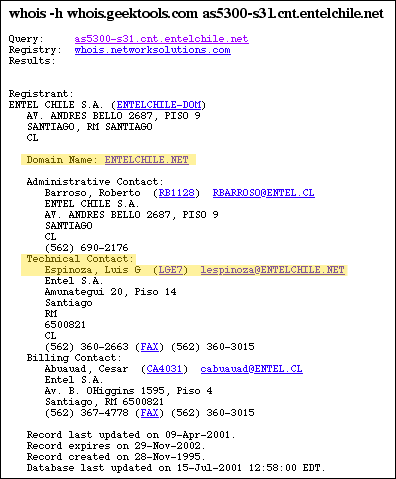
: Here's what it turns up - definitely some good stuff,
although it lacks some
: of the conveniences of western telecom's whois entries i.e. "abuse@telecom.com"
: addresses. It does turn up the address of a technical contact and
their
: web address. Those are the best way forward if you want to get a response,
: in my opinion. Don't get your hopes up that you'll see immediate results
: after contacting them - ISPs get snowed with complaints, so the best
you
: can do is to pass along a detailed message and attach the offending
bit
: of mail you're miffed about.
samSpade_geektools.gif
: Now that we know a little bit about who's system is
being hijacked to
: proliferate the Hybris worm, we can contact them directly and notify
: as such. Hopefully, they'll get around to fixing the problem. If you
: keep getting spammed, and the ISP is unresponsive, keep bugging
: them about it! Just forward every piece of spam from their system
to
: their contact person and eventually, you'll get some action. Meanwhile,
: keep a log of all email you send them - if need-be, you can get legal
: or political on their ass (which requires a paper-trail).
: Making contact with the Telecos.
|

